It is possible to monitor and control float trucks, public bus or delivery vans from the internet, obtaining their speed, position, and a lot other parameters. You can even control some parameters of the vehicle or hack into the canbus of the vehicle remotely.
Those vehicles have a Telematics Gateway Unit (TGU) device and a 3g/4g/gprs/lte/edge/HDSPA modem to connect to the internet, with a public I.P. address.
There are thousands of TGU connected to the internet, with no authentication at all and with administrative interfaces through a web panel or a telnet session.
Finding publicly exposed TGUs in the internets
There are tons of open TGU and similar vehicle appliances on the internet. One very interesting and easy to find is the c4max.
The c4max smartbox is a TGU with powerful capabilities, a simple console on port 23, and is easy to identify while scaning the internet.

A quick search with shodan, reveals 733 open c4max devices on the internet, at the time of scanning. Because of the nature of these devices, connected to the internet using mobile data plans and in industrial vehicles, the devices you can find vary a lot from time to time.
Scanning the internet yourself with masscan finds different industrial vechicles working at different hours.
The c4max can be found looking for port 23, and the banner ‘gps’ or ‘welcome on console’ or similar strings from the telnet console they provide.
An example with shodan:
https://www.shodan.io/search?query=port%3A23+gps+%22on+console%22
What can be done inside a c4max TGU
The c4max devices that I found on the internet are not password protected, and there is no security that prevents anyone from connecting to them.
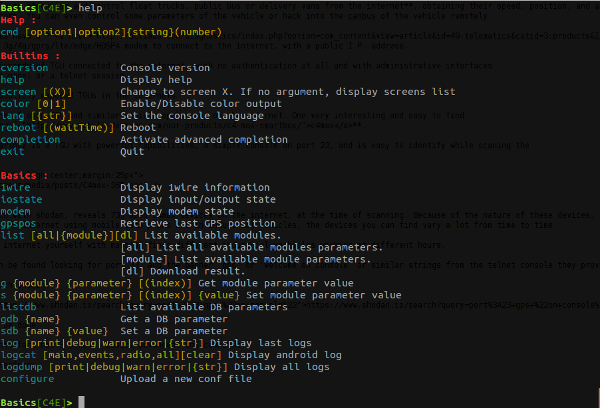
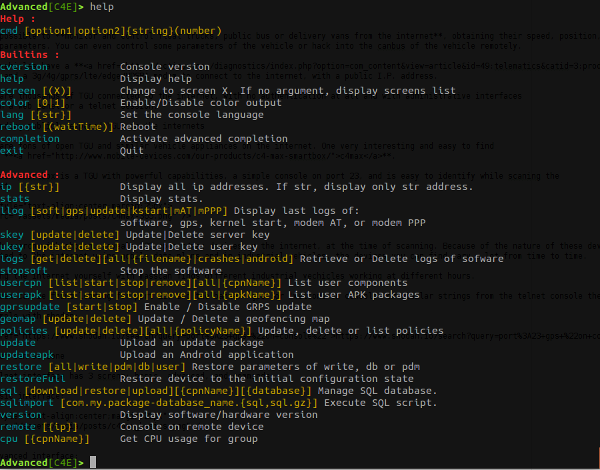
The telnet interface has 3 screns: basic, advanced, and commands.
The basic interface:
The advanced interface:
Commands:

Some interesting commands:
Basics[C4E]> iostate
Input 1 : Disconnected
Output 1 : Disconnected
Output 2 : Disconnected
Alarm : Disconnected
Ignition : Connected
Basics[C4E]>
Retriving gps coordinates of the vehicle (removed some info from the output, replaced by XXX…):
Basics[C4E]> gpspos
Internal antenna
GPRMC Frame value is
$GPRMC XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
GPGGA Frame value is
$GPGGA,XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
Basics[C4E]>
And with the gps coordinates, we can locate the vehicle in google maps, for example:
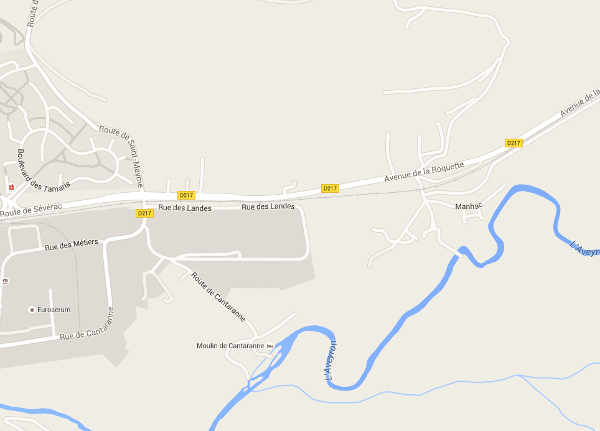
List available modules:
Basics[C4E]> list
dbg
pdm
sql
wdg
boot
dhcpServer
sshTunnel
serialPPP
cpnManager
netMonitoring
boardsInfo
messageBrokerProxy
versionManager
messageBroker
config
dnsProxy
fileManager
dictionary
can
gps
ios
usb
bootReason
batt
leds
onewire
wifi
smartCardManager
j1587
j1708
j1850
j1939
kline
modem
nvram
usbHfk
chronoTachyGraph
sensors
dtc
jvm
obd
ibutton
dataEmitter
jbinaryGate
ledManager
network
adminProtocol
crashSensor
timeZoneManager
instantFixII
modemOperatorDriver
gpsOdometer
smartSensors
relayControl
driverBehavior
obdStacks
locales
fileSync
pwrManager
gpsMvtDetector
geoFencing
sensorsCalibration
updateManager
companionSoftwareClient
urlServer
gpsEcho
binaryGateMonitor
sensorsRecorder
messageGate
binaryGate
deadReckoning
speedDropControl
criticalCommandManager
cacheManager
update
acceleroMvtDetector
history
commandManager
dataRecorder
eeprom
Basics[C4E]>
The can bus module:
Basics[C4E]> list can
com::mdi::drivers::can.activateDebug=0
com::mdi::drivers::can.active_protocols=255
Basics[C4E]>
And with listdb, we can get a lot of information from the vehicle, the company that operates the vehicle, the driver etc, that I will not post here, for obvious reasons, but some of the information form listdb:
...
MDI_EXT_BATT_VOLTAGE='12687'
MDI_GPS_SPEED='0000090'
...
Modem information:
Basics[C4E]> modem
ppp0 XXXXXXXXXXX
APN: XXXXXXXXXXX
autoAPN: XXXXXXXXXXX
Your IMEI is : XXXXXXXXXXX
Your IMSI is : XXXXXXXXXXX
DNS servers are
nameserver XXXXXXXXXXX
nameserver XXXXXXXXXXX
In case of problem, check your configuration (with "list all" command)
Basics[C4E]>
We can even geofence the vehicle (I don’t know what it would cause):
com::mdi::services::geoFencing.periodInMs=5000
com::mdi::services::geoFencing.directory[0]=/mnt/user/writeDir/geofencing
com::mdi::services::geoFencing.directory[1]=/mnt/user/data/geofencing
com::mdi::services::geoFencing.directory[2]=/mnt/user/mmc/geofencing
com::mdi::services::geoFencing.areaModeSearch=0
Conclusion
Telematic Gateway Units exposed to the internet with public addresses and no authentication can be used to remotely track industrial vehicles, geofence them, change the mission route, if you read the schematics of these units:
http://www.neweagle.net/ProductDocumentation/Telematics/C4MAX_datasheet.pdf
You can see this device is connected to the bus of the vehicle, to the ignition, to the battery… and the theoretical things that could cause are very scary. Of course, not having one of these available and just testing in the wild is not responsible and of course I will not do it, so I still don’t know how far one can go with access to one of these devices. Caution is advised.
IMPORTANT NOTE: ALL THE INFORMATION CONTAINED IN THIS POST IS INTENDED FOR EDUCATIONAL AND RESEARCH PURPOSES ONLY. MANIPULATING REAL AUTOMOTIVE DEVICES FROM THE INTERNET IS NOT ETHICAL AND COULD BE ILLEGAL UNDER YOUR JURISDICTION. ANY VIEWS OR OPINIONS EXPRESSED IN THIS ARTICLE ARE ONLY MY OPINIONS AND NOT RELATED TO MY EMPLOYER OR ANY ORGANIZATION I BELONG TO. ALL THE INFORMATION PROVIDED IN THIS POST HAS BEEN COLLECTED USING PUBLICLY AVAILABLE RESOURCES, LIKE MANUFACTURER MANUALS AND SPECIALIZED SEARCH ENGINES. IN THE COURSE OF THIS FINDINGS, THE DEVICES DESCRIBED HERE NEVER HAD ANY KIND OF SECURITY IMPLEMENTED TO PREVENT CONNECTIONS TO THE DISCOVERED INTERFACES AND THEIR SECURITY WAS NEVER CIRCUMVENTED OR BYPASSED.
